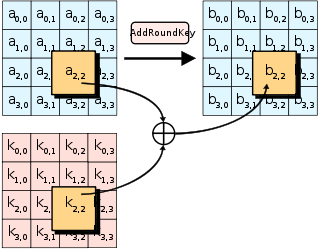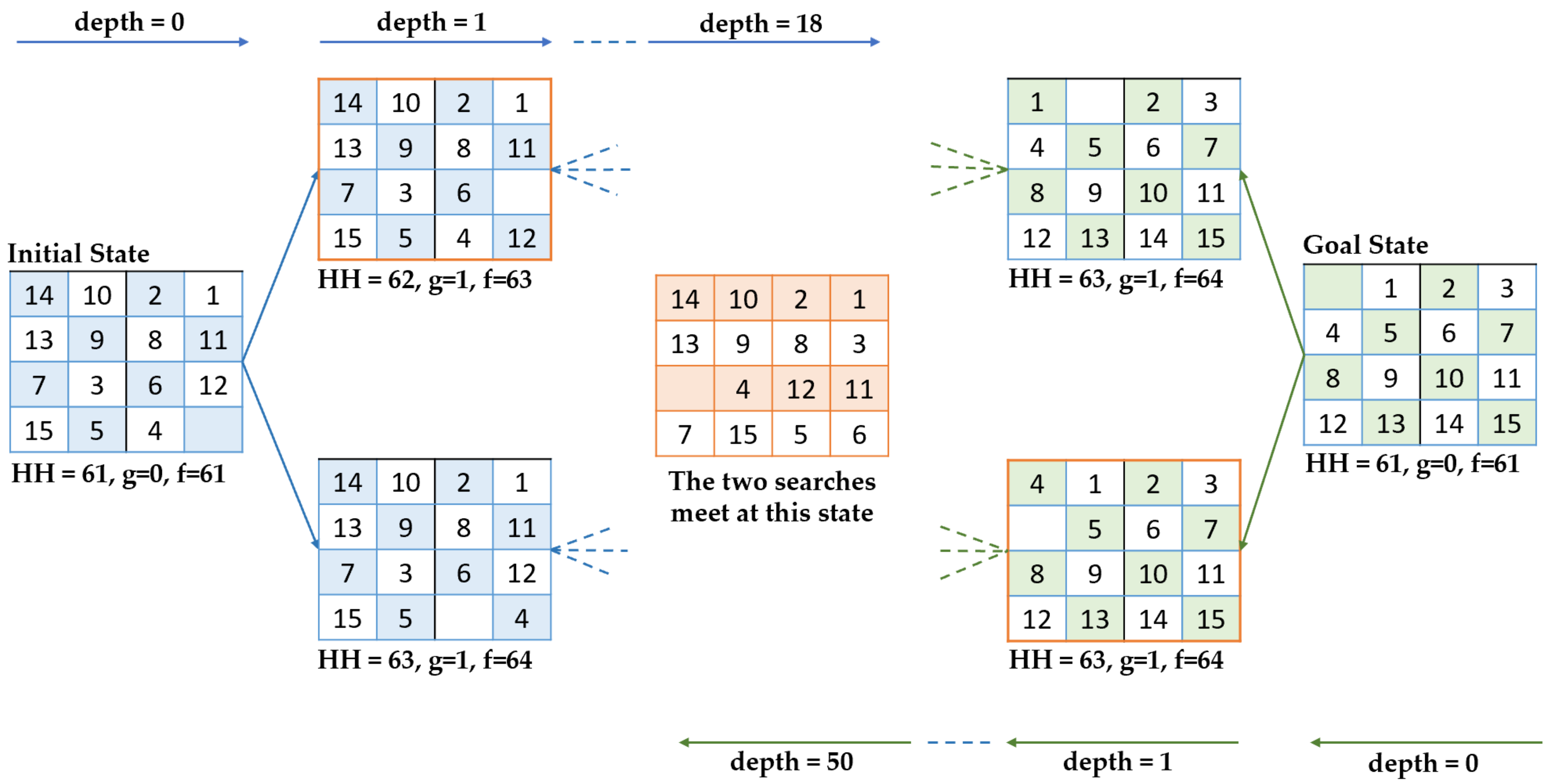
Computers | Free Full-Text | The Fifteen Puzzle—A New Approach through Hybridizing Three Heuristics Methods
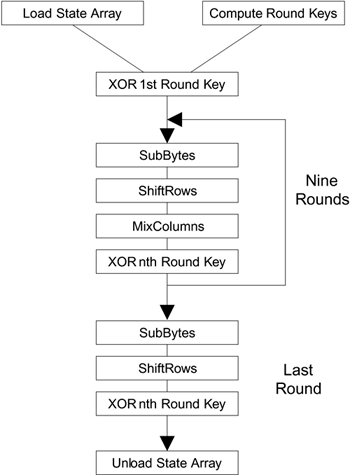
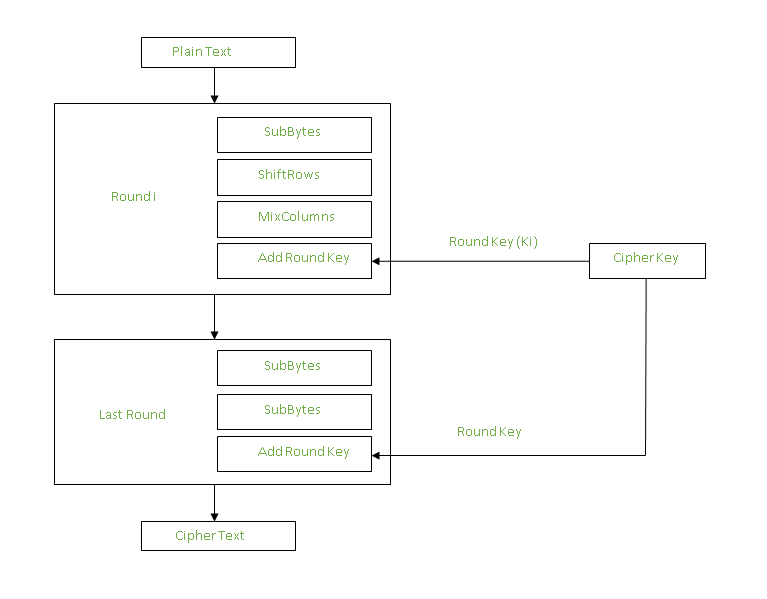
Steps in the AES Encryption Process :: Appendix A. Overview of the AES Block Cipher :: Appendixes :: 802.11 security. wi-fi protected access and 802.11i :: Networking :: eTutorials.org


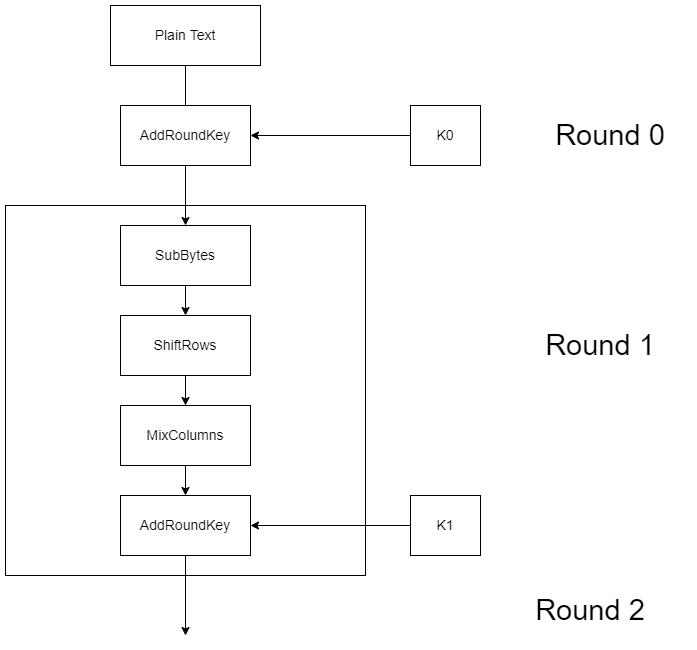

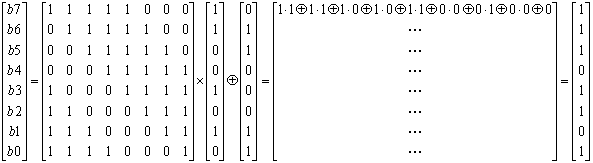
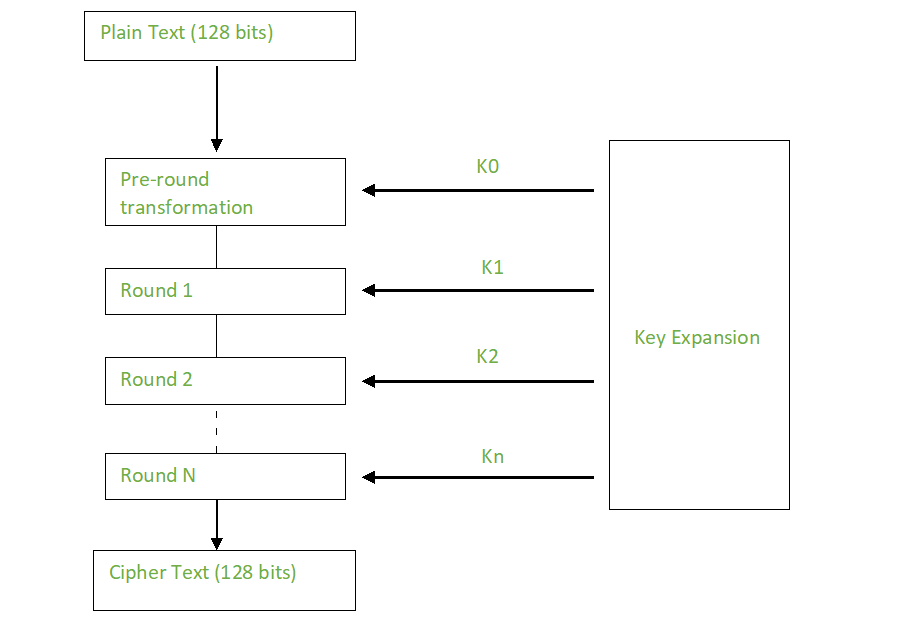


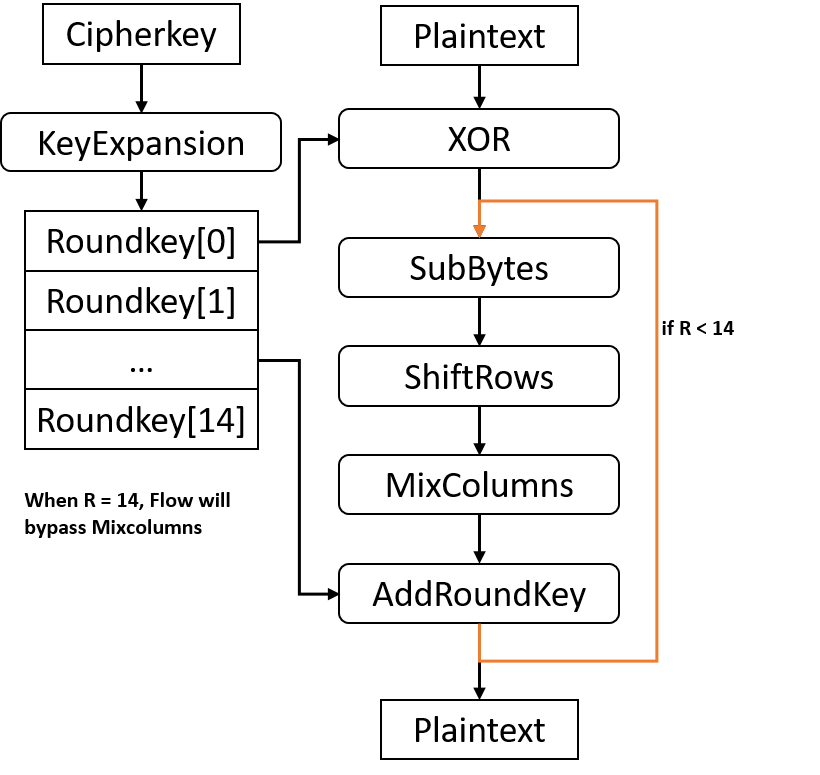


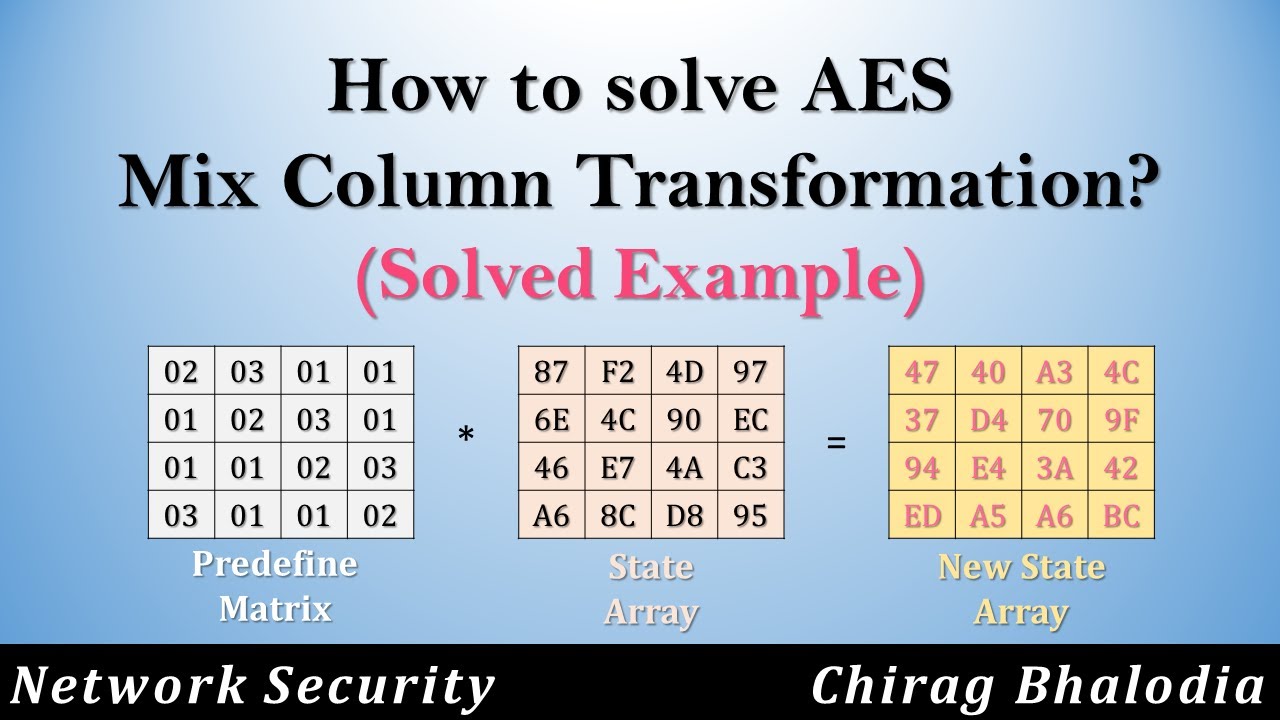

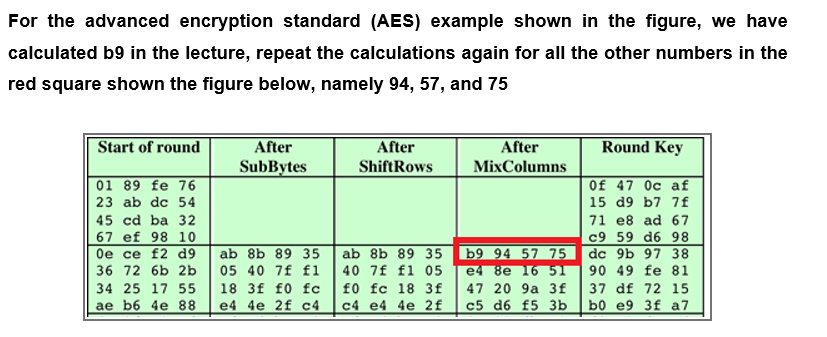
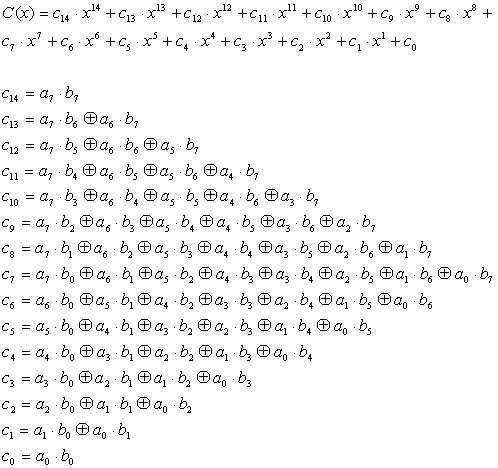
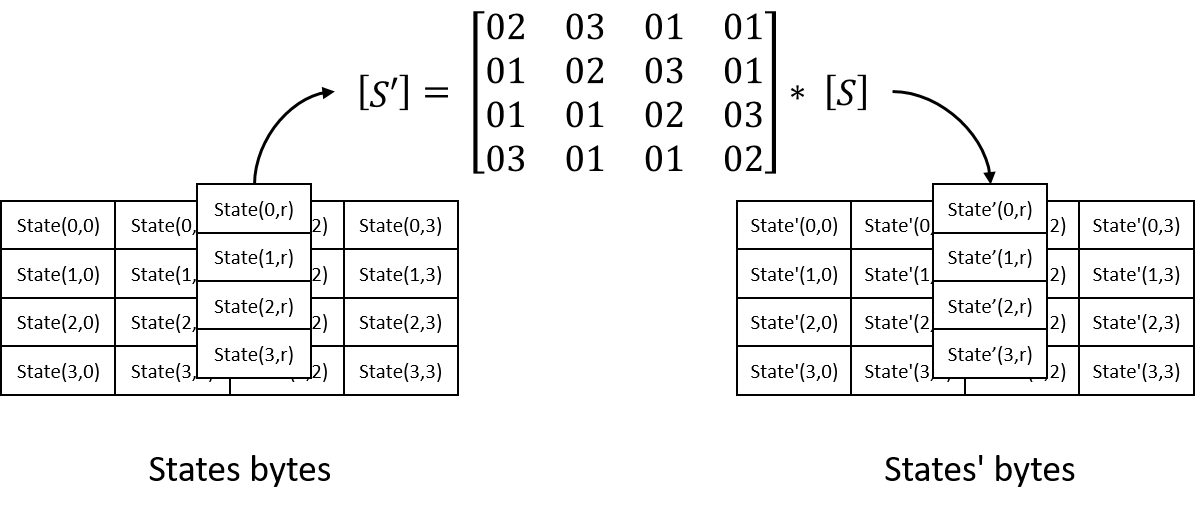
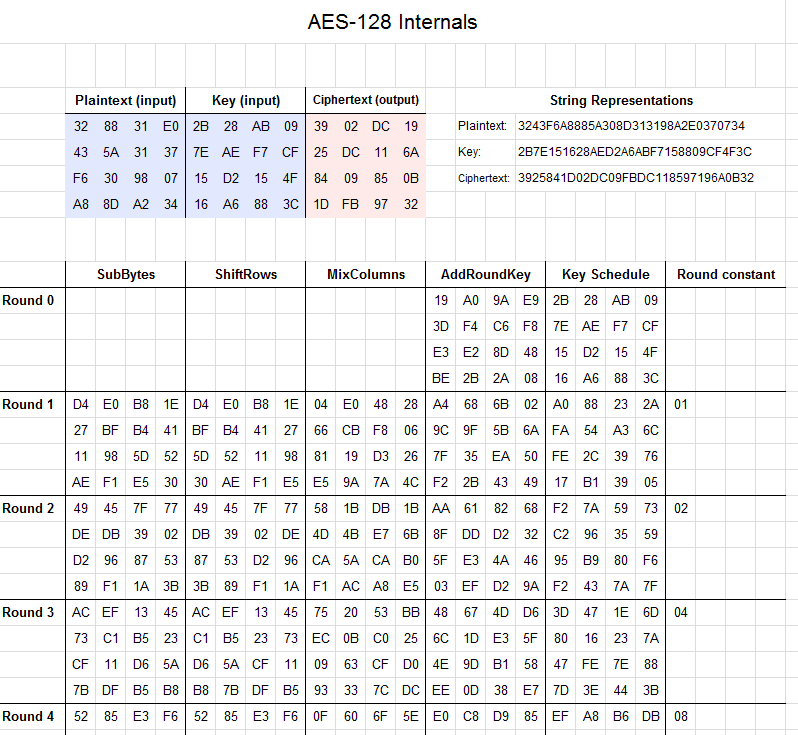
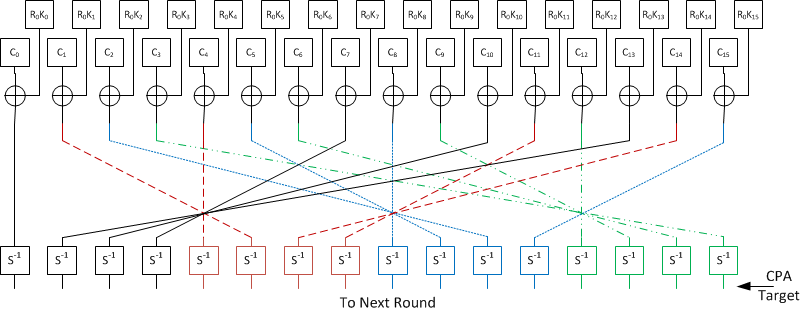

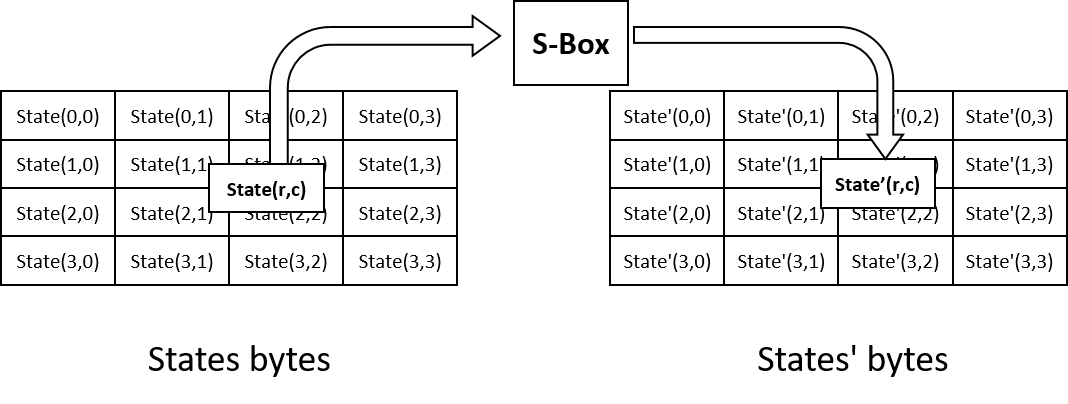
![PDF] High-level simulation for side channel attacks | Semantic Scholar PDF] High-level simulation for side channel attacks | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/f3a5ceffa907e5b328900d0891d38acc867db710/2-Table1-1.png)